SC-200: Security Operations Analyst (4 Days)
Price:
Course Length – 4 days
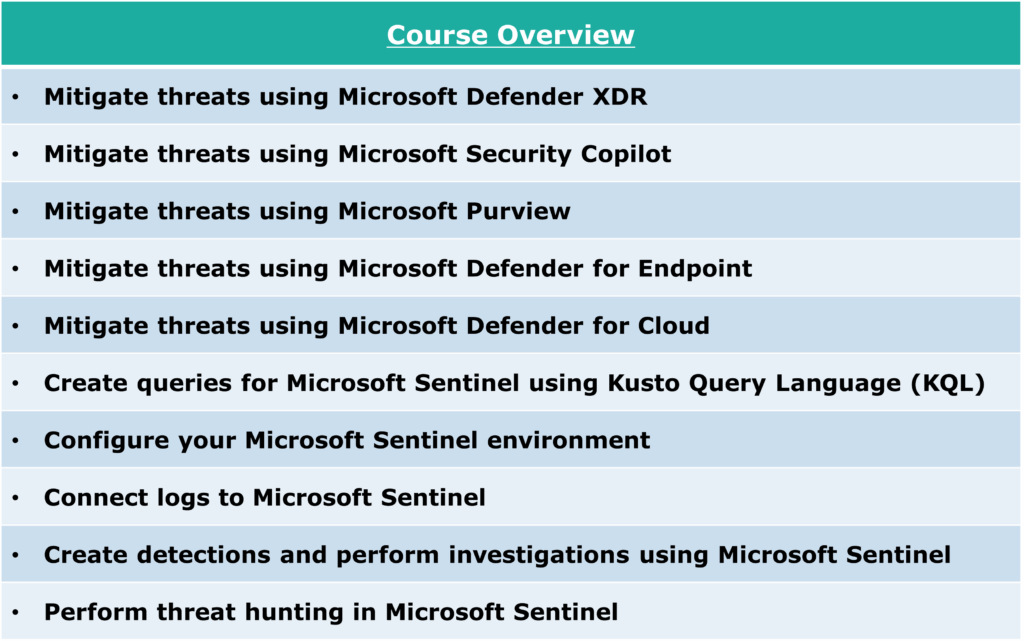
Develop skills to investigate, search for, and mitigate threats using Microsoft Sentinel, Microsoft Defender for Cloud, and Microsoft 365 Defender. Learn how to perform triage, respond to incidents, and hunt for threats using security intelligence.
SC-200 is a dynamic course targeted at emerging cybersecurity professionals who aspire to master the operational techniques required to monitor, detect, and respond to threats in a Microsoft environment. With a curriculum that marries theory with extensive hands-on practice, this course provides an in-depth exploration of modern security operations centers (SOCs) and the tools that enable them, such as Microsoft Sentinel, Microsoft Defender for Cloud, and Microsoft 365 Defender. Learners will gain critical insights into incident response, threat hunting, alert triage, and investigation methodologies, addressing how to identify vulnerabilities and neutralize risks in real time. Detailed case studies and simulations of live security incidents further equip professionals with the skills to analyze and remediate breaches, fostering a proactive security mindset.
By the end of the course, participants can confidently implement and manage advanced security solutions, ensuring robust defense mechanisms that bolster the overall security posture of any enterprise landscape.